Revision: 2024-04-08
Some authentication methods use email sending and the user's email address in the authentication and/or setup flow. Document Control does not store or record the email addresses of Confluence users. When Document Control needs access to the email address, the email address will be retrieved on demand from the Confluence API. That means Document Control always uses the user's current email address as it is registered in Confluence and the Atlassian user account. The user's organization and/or the user have full control over the email address, and Document Control can not change it. For some authentication methods, the user's Atlassian registered email address is compared to an external email address (e.g. for SSO). When this comparison is done, Document Control will lower case the email addresses before comparison (e.g. "Jane.Anderson@example.com" and "jane.anderson@Example.COM" are considered equal).
Users can view their Atlassian registered email address at their Atlassian profile page.
A Personal Token is a code or password a user needs to set up before the first use. When you enable this authentication method, users without such a token are prompted to create it. Token creation is validated by a short lived code sent by email, and token deletion triggers a warning email to the user.
Token usage and misuse is protected by rate limiting, and if too many incorrect tokens have been tried, the user is prompted to reset the token.
For 2FA authentication, a user needs to install and pair an authenticator app. Compatible apps are:
API key: When using API key authentication, a user needs to generate a secure token once by using the Atlassian provided secure token management page at the Atlassian API token page. The token is unique to each user, and can be revoked on demand.
The email for the signature must be the email address used for Confluence login.
Single Sign-On (SSO) is supported through OpenID. Document Control works with many OpenID authentication providers, e.g. Okta and Microsoft Entra ID (Azure AD).
The configuration for OpenID requires multiple OpenID provider settings. These settings depend on your organization's OpenID setup.
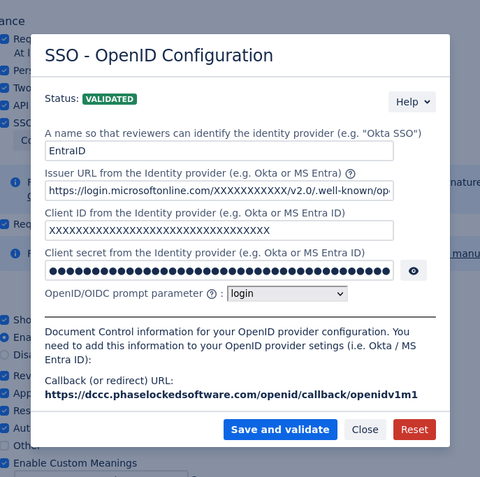
Setting up OpenID requires you to provide Document Control with the OpenID provider's information, and also requires you to provide specific Document Control settings to your OpenID provider.
As part of the setup process, you will be redirected to your OpenID provider to check if all settings are correct.
https://dccc.phaselockedsoftware.com/openid/callback/openidv1m1The callback URL might change with e.g. data residency changes.
Regulatory Compliance: When using OpenID, Document Control uses an external authentication provider for user authentication for the signatures. Document Control does not control the settings of the external authentication provider, and it is your responsibility to validate the authentication settings to ensure regulatory compliance. Document Control protects the integrity of the signature information in the authentication process, however Document Control can't guarantee the integrity of the authentication request. It is your responsibility as user of Document Control to validate the authentication flow with the applicable regulatory regulations.
https://login.microsoftonline.com/XXXXXXXXXX/v2.0/.well-known/openid-configuration.https://XXXXXXXXXX.okta.com/.well-known/openid-configuration.